Block App Open Screen Ads on iOS
Chinese internet companies really have no shame. They came up with this shake-to-display ad that redirects you to an advertisement page just by shaking your phone. I almost fell for it, but going back to an older version of the app on iOS is too complicated. I couldn't stand it anymore, so I eventually decided to capture the network traffic and used Shadowrocket's rules to block these disgusting ads.
This post was translated from my Chinese blog post with the aid of ChatGpt.
The principle behind this method is to utilize Shadowrocket’s “REJECT” rules to intercept and block requests to ad domains made by the app, returning a 404 status code. As a result, the app won’t be able to retrieve the ads, and consequently, they won’t be displayed.
Note: This method requires the following:
- An Apple ID registered in the US/UK region and corresponding payment method, as the effective proxy apps have been removed from the Chinese App Store.
- A reliable VPN service or VPS, as you’ll need to keep the VPN active continuously.
- Reinstallation of the app you want to block ads for.
Importing Rules
Here, I’ll use Shadowrocket as an example, but the configuration process is similar for other proxy apps like Quantumult X, Surge, etc.
First, set Shadowrocket’s “Global Routing” to “Config”.
Then, go to “Config” and add a rule. There are many rules available on GitHub. I’m using the “Blacklist + AdBlock” from the following rule set:
Installing Packet Capture App
Even though the imported rules can already block some apps’ splash screen advertisements, there are apps whose ad download links change frequently and might not be covered by the rules. For these cases, you need to capture those links using a packet capture app and then add them to Shadowrocket’s rules.
For users in the Chinese region, a recommended packet capture app is Stream. However, it’s not available in the English region. For this purpose, I’m using Storm Sniffer.
Adding VPN
When you launch the app for the first time, toggle on the “Enable Packet Capture” switch. You’ll then be prompted to add a VPN configuration. Allow the configuration and enter your device’s password.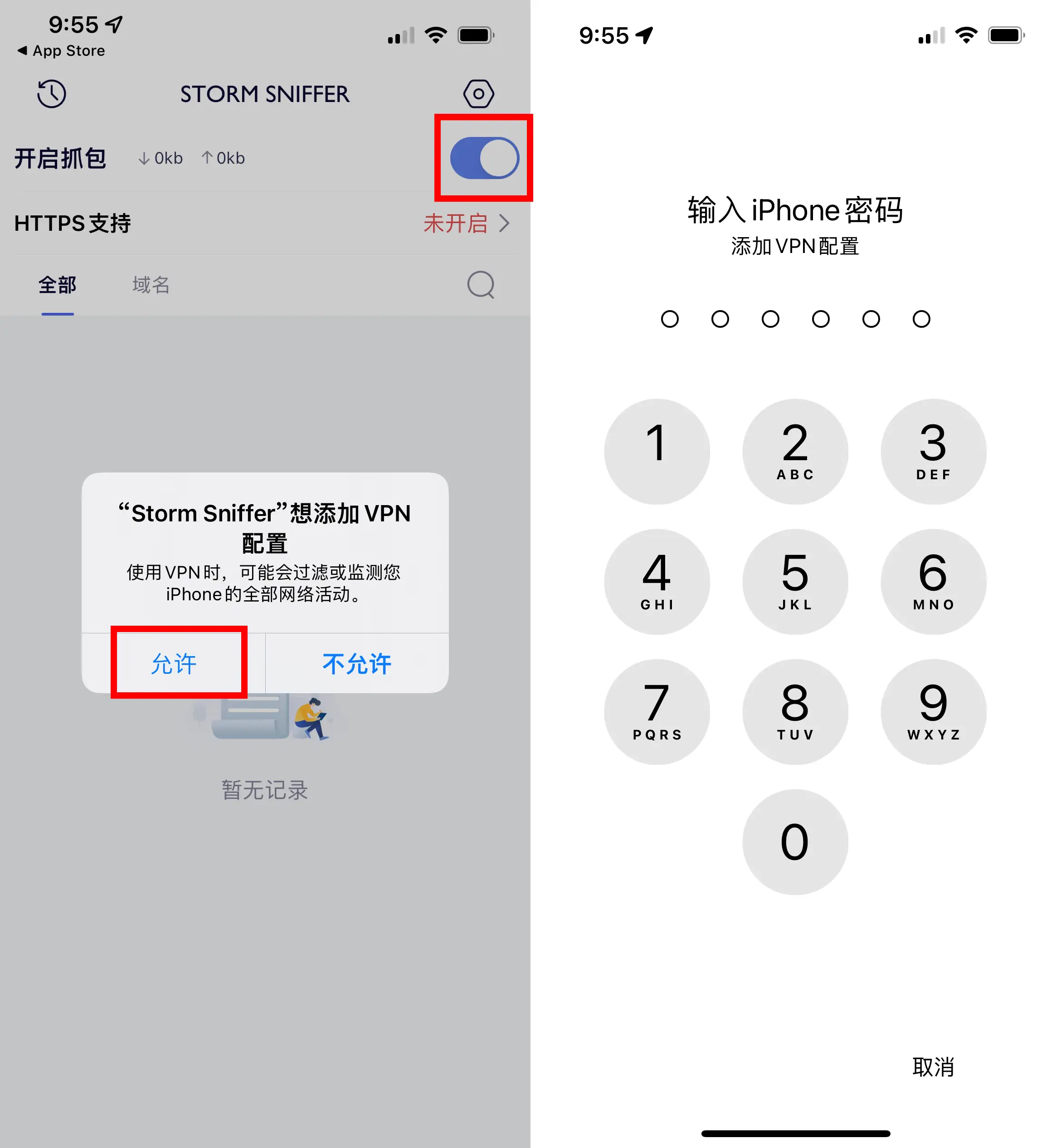
Enabling HTTPS Support
The next step is to enable HTTPS support, which involves downloading and enabling a certificate.
Downloading the Certificate
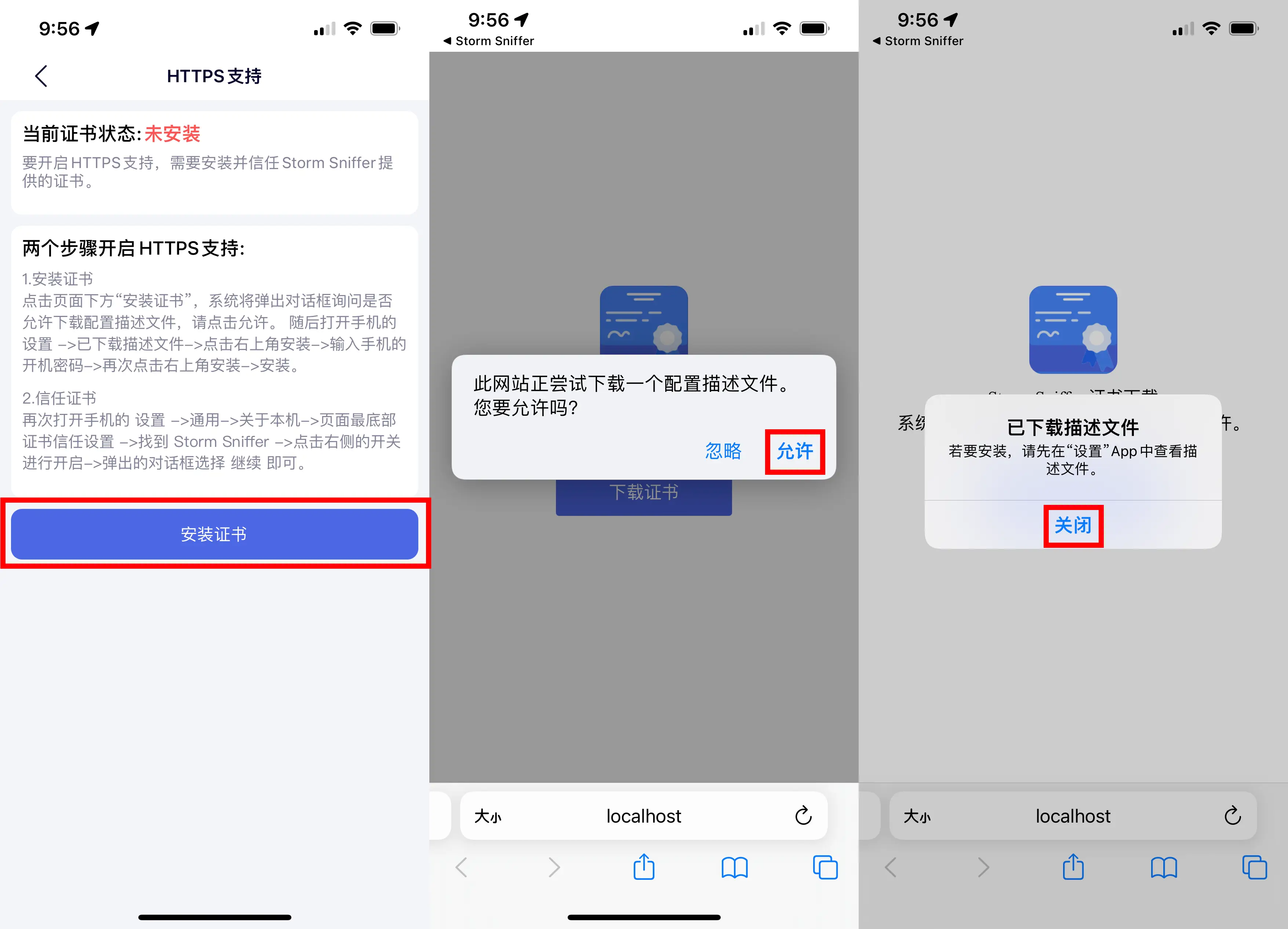
Installing the Certificate
After the download is complete, open Settings, and you will see a new entry called “Downloaded Profiles.” Click on it and then tap “Install” in the upper-right corner. Enter your password, and a warning about trusting the certificate will pop up. Continue by clicking “Install” again.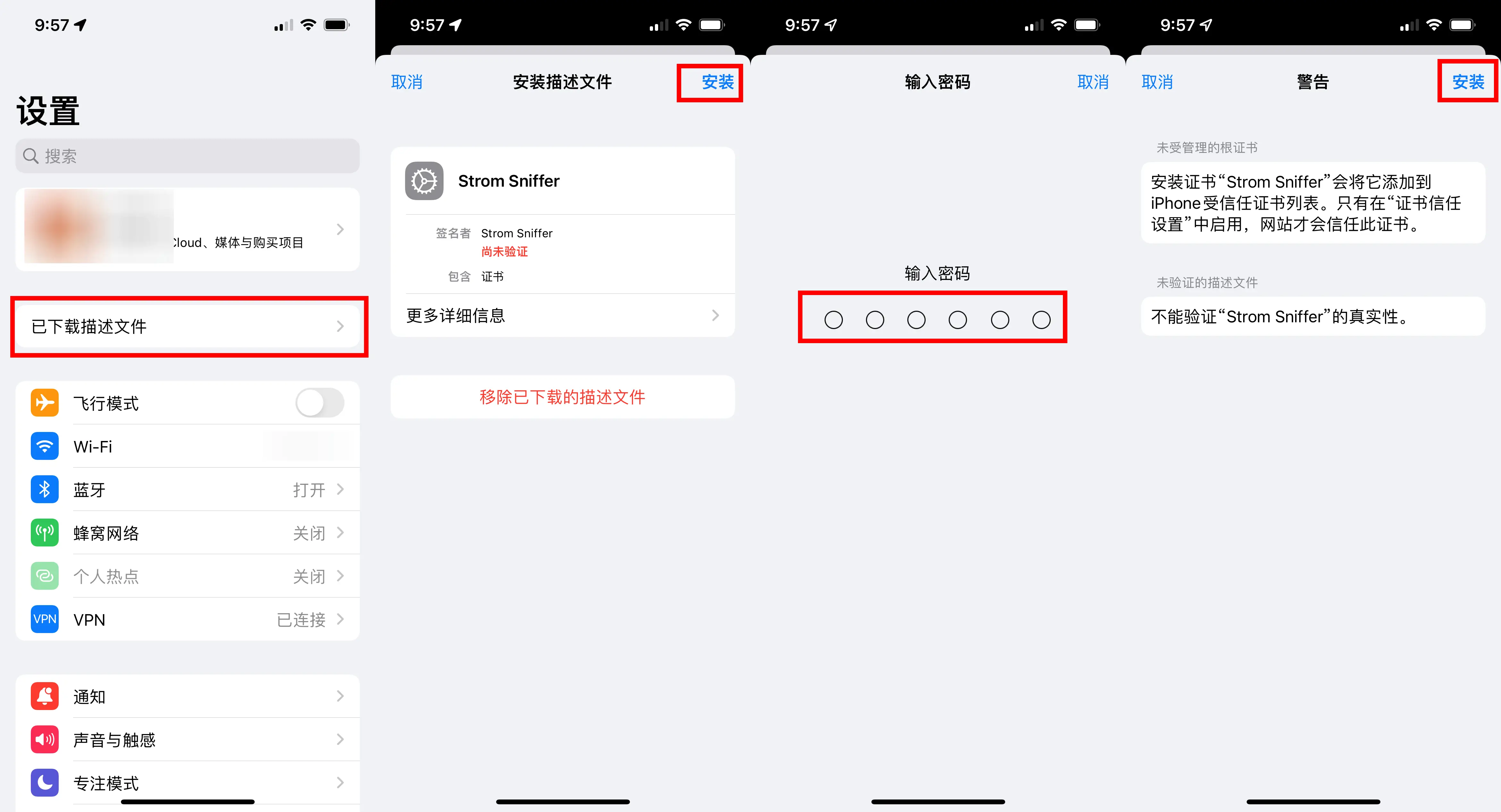
Enabling the Certificate
Open “Settings,” then go to “General” > “About.” Scroll down to the bottom and find “Certificate Trust Settings.” Enable the certificate for Strom Sniffer. Note that the certificate’s name slightly differs from the app’s name. You’ll see a warning; click “Continue” to proceed (it’s recommended to disable it after capturing packets, though). Return to the Storm Sniffer interface. If it looks like the image on the far right, it means that HTTPS support has been successfully enabled.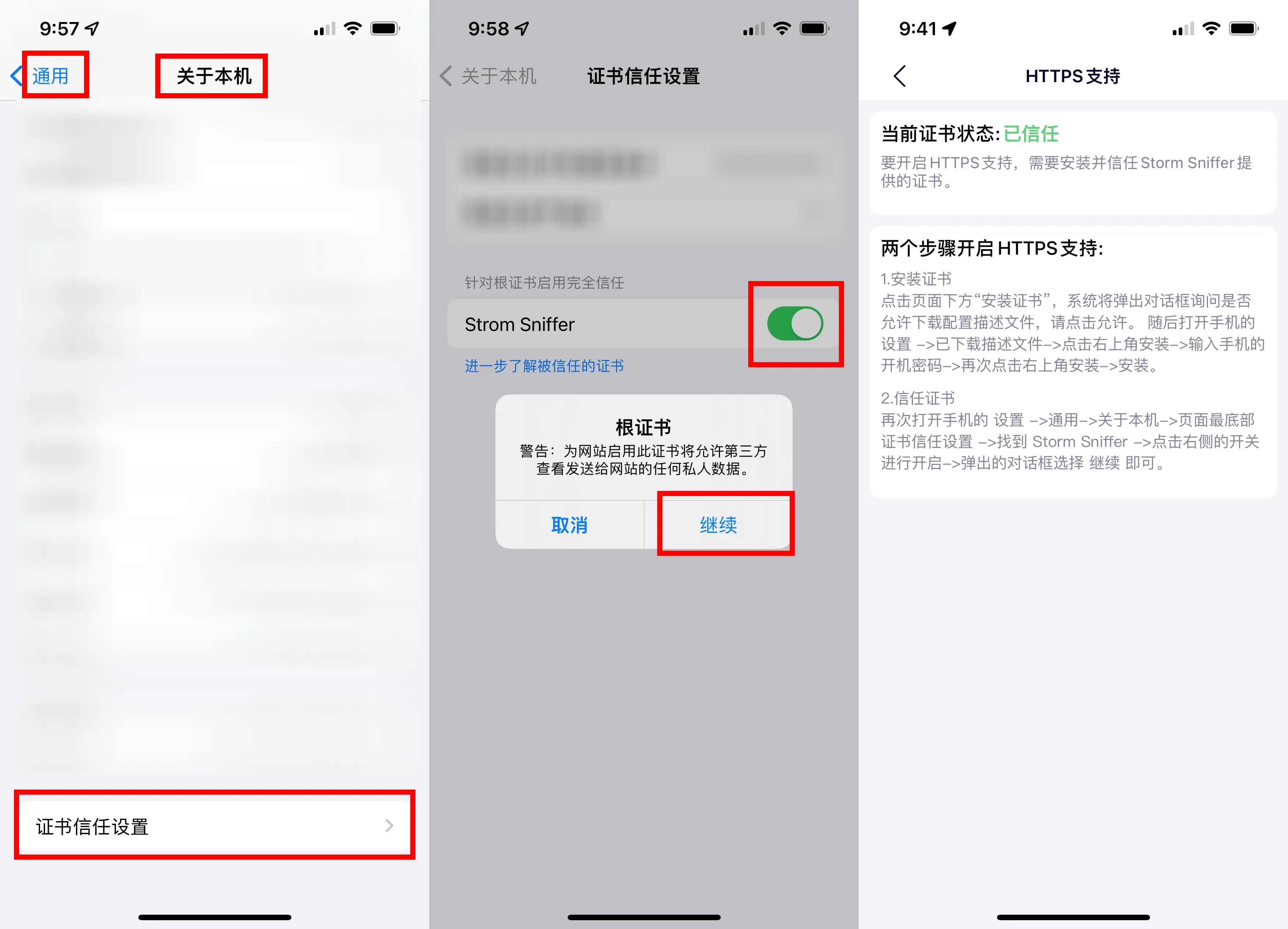
Deleting the Certificate
Deleting the Certificate
For a complete cleanup, you can go to “Settings” > “General” > “VPN & Device Management,” find Strom Sniffer, and then tap “Remove Profile.”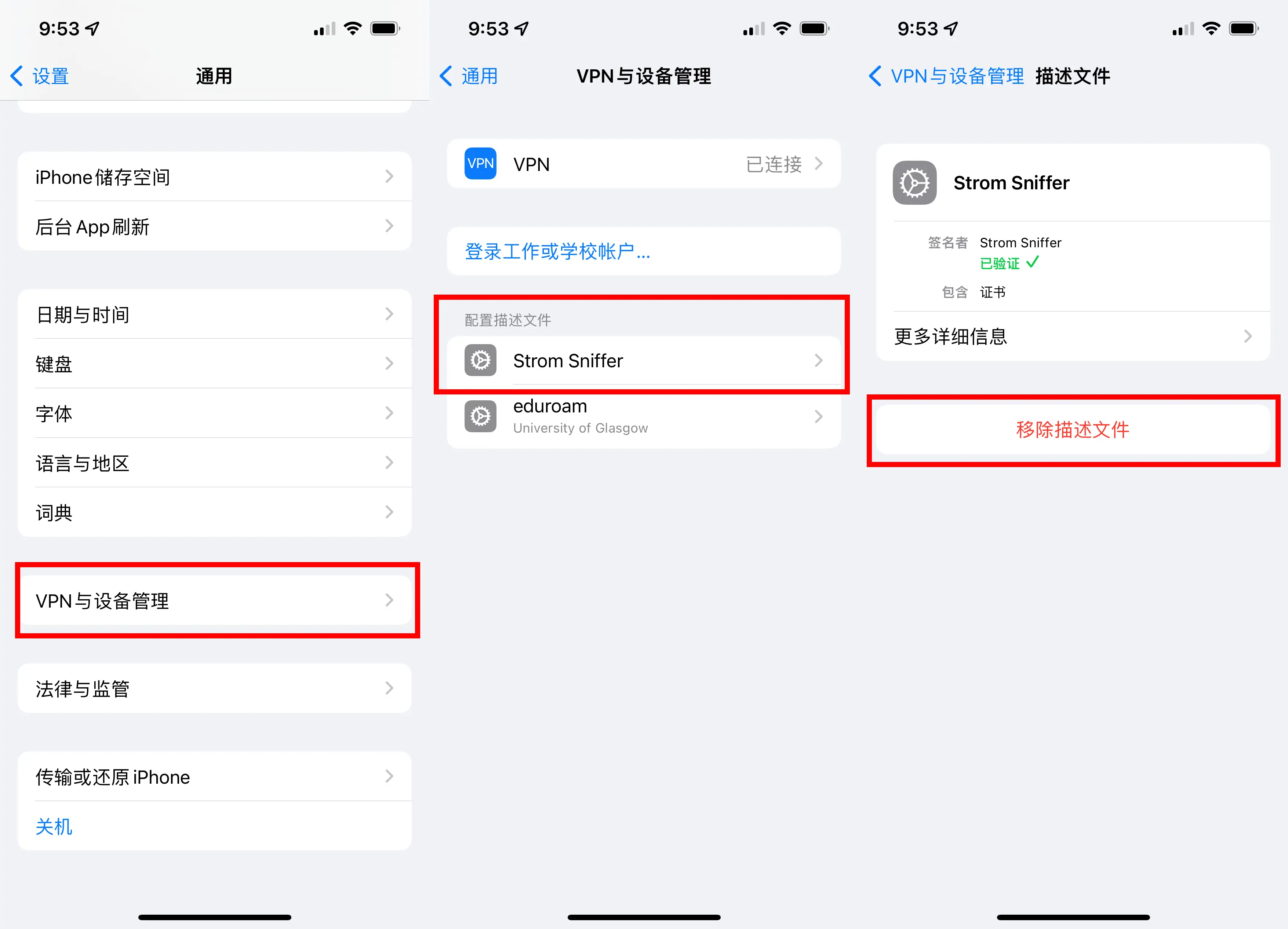
Capturing Packets
Before capturing packets, it’s necessary to uninstall and reinstall the app you want to capture packets from. This is because the ad files are already in the app’s cache. The app’s supposed “clear cache” function doesn’t clear the cache for ads. When the app launches, it directly uses the cached ads without making requests to the ad server. Without these requests, we can’t capture the ad server’s domain names, and consequently, we can’t block them.
First, open the “Enable Sniffing” switch in Storm Sniffer. Then start the app you want to capture packets from. Ads might not pop up the first time you launch the app. Try clearing the app from the background and launching it a few times. Once the ads load, return to Storm Sniffer, turn off the “Enable Sniffing” switch, and then search the list for domain names that resemble ads. Image-based ads are easier to spot since Storm Sniffer shows a preview. For video ads, you’ll need to search more carefully. Once you find the domain, tap the HOST of the request in Storm Sniffer, choose “Copy Value,” and you’ll copy the domain name.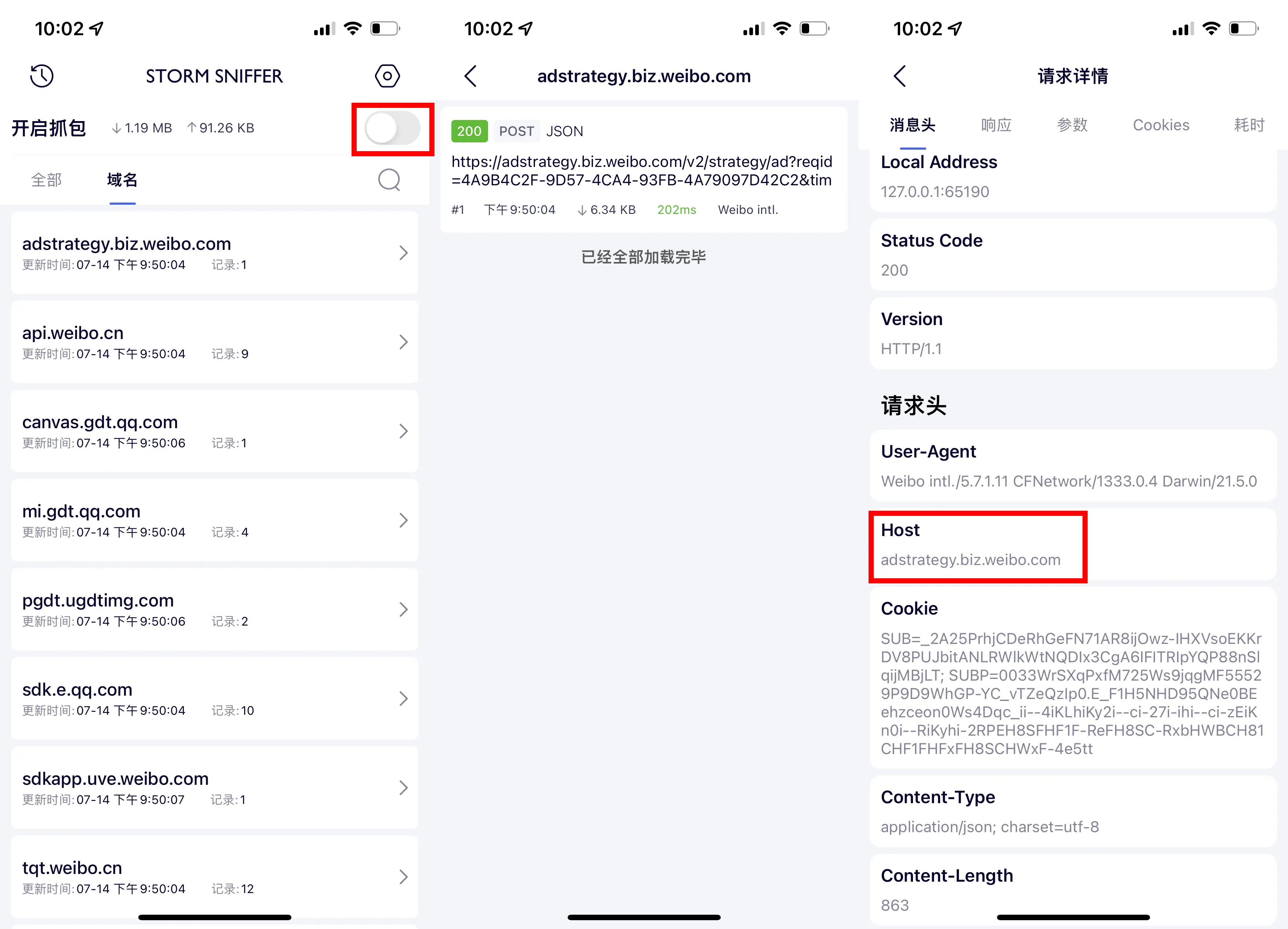
Adding Rules
Open Shadowrocket’s “Config,” then open the previously imported rules. Click the plus button in the upper-right corner to add a new rule. You generally don’t need to change the type; set the strategy to “REJECT,” and paste the domain name you just captured. Save the rule.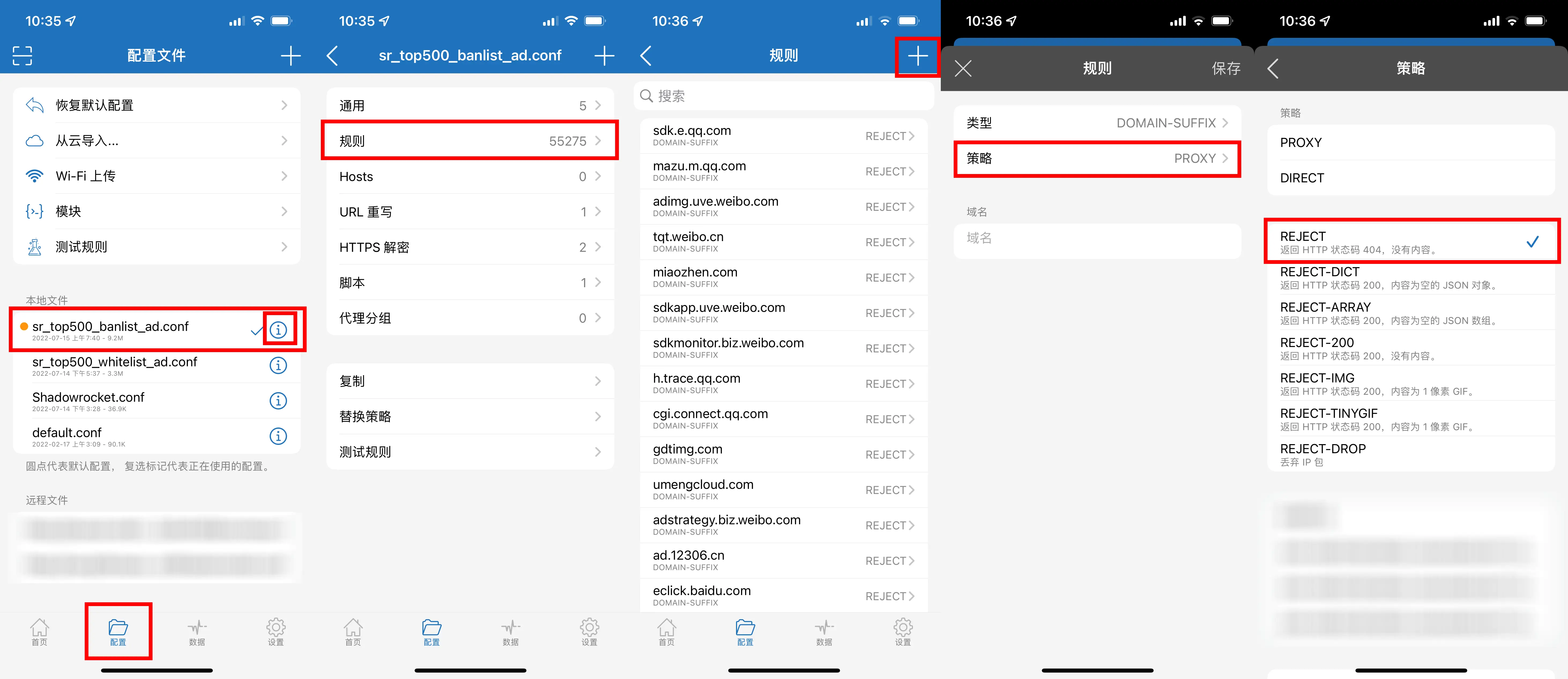
Then enable Shadowrocket’s proxy. Reinstall the app you captured packets from, clear the ad cache, and you should be able to use the app without the ads.
Rule Types
Rule Types
Explanation of Some Common Rule Types
- DOMAIN: Domain matching
- DOMAIN-SUFFIX: Domain suffix matching
- DOMAIN-KEYWORD: Domain keyword matching
- IP-CIDR: IP range matching
- GEOIP: GEOIP database (country code) matching
- DST-PORT: Destination port matching
- FINAL: Remaining websites
Murmur
In order to display ads, Chinese apps really go to great lengths. The domains for the ads in these apps may change, and while the frequency isn’t high, each time they change, we have to reinstall the app and capture the new domains, which can be quite troublesome. However, once the blocking is done, we no longer have to endure those 5-second splash screen ads. The apps launch instantly, and we don’t need to worry about those annoying faces of unwanted ads popping up on the splash screen. It’s definitely worth the effort. Additionally, here’s a list of blocked domains for the international version of Weibo.
Blocked Domain List for Weibo International Version
- sdk.e.qq.com
- mazu.m.qq.com
- adimg.uve.weibo.com
- tqt.weibo.cn
- miaozhen.com
- sdkapp.uve.weibo.com
- sdkmonitor.biz.weibo.com
- h.trace.qq.com
- cgi.connect.qq.com
- gdtimg.com
- umengcloud.com
- adstrategy.biz.weibo.com
Remember not to launch this app without the proxy enabled! Otherwise, the ads will be cached again, and you’ll have to reinstall it once more.
It’s recommended to disable background refresh for these apps. iOS’s push notification mechanism doesn’t require them to refresh in the background, and disabling it won’t affect receiving messages. After all, proxy apps may not always be stable. If the proxy fails, these apps might cache ads in the background.